Hola! welcome to the next part of my deep dive into Info-Stealers.
If you’re new to Info-Stealers, i recommend checking out this introductory post (The Silent Predators in Your Browser) for an intro.
Alright, here's actually a follow-up on what we've previously learned and know about Info-Stealers, and I thought it’d be cool to show you exactly how real Info-Stealer logs look.
It's not super technical or a long read, pretty straightforward actually. Don’t worry as i’ll guide you step-by-step and give you a real glimpse into what the cybersecurity world actually looks like behind the scenes.
Notes: “Logs” or “info-stealer logs” refer to text (or sometimes CSV) files that contain user credentials along with the associated url or websites. These are typically formatted as either (username:password) or (url:username:password).
Alright, let’s dive in!
Long story short. During my research a while back, i’ve actually explored various platforms where vast collections of Info-Stealer logs are widely shared and distributed daily.
Some of these logs are freely accessible and offer general data (likely from regular users without privileges or valuable access), while others require a paid subscription and often containing more sensitive information from high-level accounts or private platforms.
Just to be clear, we’re not examining the Info-Stealer malware itself here; instead, we’re focusing on the data or credentials it has gathered from victims’ browsers or machines. So without saying much, let’s dive in as i take you through these logs, revealing what Info-Stealer data actually holds and why it matters.
Disclaimer time...
⚠️ Disclaimer ⚠️
No payments or subscriptions were made to obtain these actual "Info-Stealer Logs," and in fact, they are freely accessible and widely distributed across various online platforms and on the Dark Web, though they stay somewhat hidden.
This investigation is conducted strictly for educational purposes!
And i do not accept any responsibility for any incidents that may arise from the information i've provided here.
For this demonstration, since there are tons of info-stealer logs being freely distributed daily on the platform that i observed.
i just randomly picked two sample of logs from there, and proceeded to analyze them.
Here are the two samples that i pulled and reviewed:
- 📄 5,000+ Valorant username-password combinations
- 📄 1 Million+ Compiled browser-stored credentials
Mind you that this is just a small, tiny, random sample that i grabbed from the platforms.
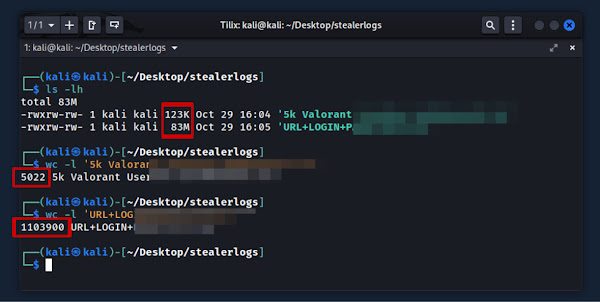
It's only 123KB in size for the 5K+ Valorant credentials and 83MB for 1 Million+ browser-stored credentials, which include data from multiple users, and not just a single victims.
These platforms are updated with hundreds of new logs every day, so there's a mind-blowing amount of stuff still buried out there.
Let’s dig into the details of these info-stealer logs, starting with an inside look at the Valorant credentials.
Seeing more than 5,000 Valorant user credentials openly available makes you wonder if they’re actually legit, right? So, i decided to test it out for you!
🎯 5k+ Valorant Credentials
Here’s a glimpse of the 5,000+ Valorant credential logs i pulled from the platform, presented unfiltered, and in their original format.
It’s likely that these logs have been compiled from the data of multiple victims affected by Info-Stealers
Upon analysis. On top of the file, there’s a note from the seller or source of these logs, followed by a lengthy list of credentials presented in the format (username:password).
Here’s where things get interesting....
So, from the extensive list of over 5,000 credentials, i manually chose a random few sample of credentials to test.
However, rather than entering the credentials directly on Riot’s (developer of Valorant) website or through the Riot client.
i decided to use a web proxy (Burp Suite), in this case, to act as a middleman and check if the credentials were valid or not.
But hold on... though, the username and password is correct.
i still haven't been able to log into these accounts yet, and do you know why?
Yep, it's because the users have enabled MFA (Multi Factor Authentication), which prevents me from logging in even though i already know their username and password.
While MFA is effective in many cases, attackers can still bypass it with several method or advanced techniques.
Fortunately, in this case, the victim's account remained secure since i didn't attempt to bypass the MFA.
Then, i continued testing other credentials from the list and.....
BOOOM!! 💥
I successfully gained access to one of the accounts! There was no MFA enabled for this account.
I knew i had full control of the victim's account at this moment. If i were a malicious actor, i could have done anything i wished with it
However, i decided to terminate the session and dropped the request before it reached the webserver,
as my objective was solely to confirm that the credentials in the free info-stealer logs were indeed valid and that some of the victims might not have their MFA enabled
Now, let's dive into the second sample of logs
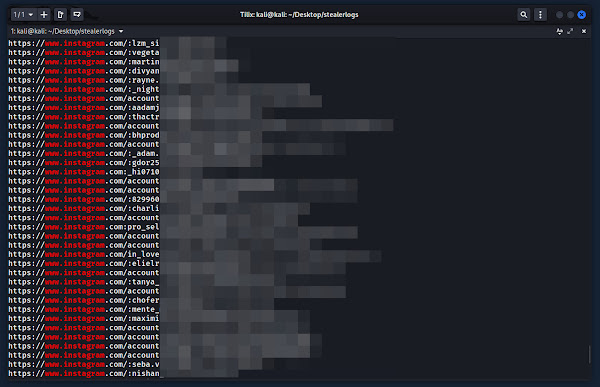
📂 1 Million+ Browser-Stored Credentials
The second log contained over 1 million browser-stored credentials.
This collection seems to include login credentials from various users across multiple platforms, such as Facebook, Gmail, Instagram, Microsoft, Netflix, PayPal, Epic Games, Online Banking, OnlyFans 😅, and many more.
basically, any site where users might have saved their login details in their browser is likely represented here.
Notes: This time, i decided not to verify the validity of these credentials due to their sensitive nature. However, i discover some interesting findings that highlight how alarming the situation truly is.
By filtering the data from the logs for browser-stored credentials associated with Instagram and Facebook, I discovered over 10,000+ unique victim Instagram credentials and more than 17,000 victim Facebook credentials in this particular set of logs alone.
And, there are likely more other logs that i haven't yet examined from the platform, which could contain even more compromised accounts.
It’s a clear reminder of how easily our social media accounts can be taken over or as most people call it, "get hacked."
In fact, a lot of the stories we hear about accounts getting hacked usually happen because of one of these simple techniques.
And that wraps up our exploration into these Info-Stealer logs......
I hope this serves as a real eye-opener for everyone, highlighting just how vulnerable our online accounts can be and how easily they can get compromised or "hacked," as many of you often say
Therefore, to keep your accounts secure, as highlighted in the analysis above
it’s crucial to enable multi-factor authentication (MFA), use strong and unique passwords for each account, regularly monitor your account activity for any suspicious activity, be cautious with links and downloads, and stay updated on the latest security threats.
I’ll see you in the next update. ciao!
⚠️ Disclaimer ⚠️
This investigation was conducted strictly for educational purposes. No unauthorized actions were performed, and no accounts were modified, or misused in any way.
All credentials tested were handled responsibly, with sessions terminated and requests dropped immediately after confirming their validity to prevent any malicious activity.














.jpg)

